Incydr provides security professionals with visibility into what data is leaving their trusted environments’ control, helps prioritize and respond to insider risk events
Code42, the Insider Risk Management leader, announced that the Code42® Incydr™ product can automatically detect data exposure movement from trusted corporate systems to unmonitored devices, such as personal mobile phones, laptops and tablets. By identifying when a file moves to an unmonitored device, Incydr alerts security teams to blindspots, with the critical context – what type of information is being exposed, from where and similar historical events – necessary to take fast action. This new detection capability uses the Incydr Trust Model, which intelligently differentiates between sanctioned and unsanctioned activity.
This press release features multimedia. View the full release here: https://www.businesswire.com/news/home/20210913005592/en/
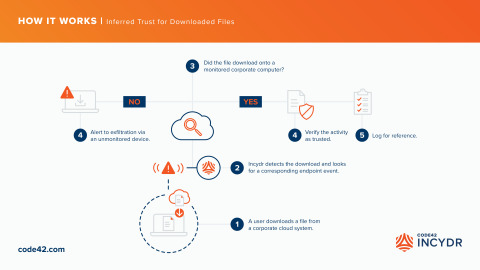
The Code42® Incydr™ product can automatically detect data exposure movement from trusted corporate systems to unmonitored devices, such as personal mobile phones, laptops and tablets. Shown in this diagram is how Incydr uses an Inferred Trust model to detect when a file is downloaded to a destination outside an organization's trusted environment. By identifying when a file moves to an unmonitored device, Incydr alerts security teams to blindspots, with the critical context – what type of information is being exposed, from where and similar historical events – necessary to take fast action. Copyright 2021, Code42 Software.
Today, 91% of information security leaders are likely to exfiltrate data from corporate systems via mobile phones. Urgency is growing to gain visibility into this activity, with more than half (56%) of security leaders saying it is a moderate or top priority to determine whether employees may be exfiltrating data this way. With the adoption of single-sign-on and cloud applications, employees are often able to sign into their corporate accounts from any device – including their personal laptops and phones. This means they have access to all types of valuable company data from their personal devices. Incydr provides visibility into these increasingly common exfiltration events.
“Trust is critical when it comes to managing risk. When insiders move company data to untrusted locations like their mobile device or their Google Drive account, they create risk for their organization,” said Joe Payne, Code42’s president and CEO. “Incydr gives security leaders the visibility to see that risk and take action to mitigate it.”
Incydr Trust Model
There are two core pillars of the Code42 Incydr Trust Model: Defined Trust and Inferred Trust.
- Defined Trust: To define the corporate environment, security teams provide Incydr with a list of “trusted” domains and Slack workspaces. This ensures file movement to these trusted destinations is viewed as sanctioned corporate activity and will not generate alerts.
- Inferred Trust: Incydr compares the activity it monitors on the endpoint with the activity it monitors inside corporate cloud systems. This innovative technology detects when files leave the boundary of trusted (monitored) locations and associates risk if a file upload or download does not reach a corporate device or cloud system. This automated comparison infers when a file has gone to an untrusted destination, such as a personal endpoint device, laptop or cloud account.
“We have taken a truly unique technology approach to solve the problem of trust,” said Rob Juncker, chief technology officer with Code42. “By correlating our visibility on trusted endpoints through our security agent and our visibility into cloud applications through our extensive API connections, we can determine when a file leaves one trusted location and does not land in another trusted location. No other vendor in security has the comprehensive view of data movement that Incydr affords.”
Availability
The Incydr Trust Model is currently available to all Incydr customers. Incydr’s ability to detect file downloads to unmonitored devices requires licensed data connectors for corporate systems and will be available beginning November.
Analysts See Trust as a New Frontier for Cybersecurity
“The risks associated with authorized users simply doing their jobs has been around for as long as we have needed to share valuable information with colleagues, clients and collaborators. The difference now is that both the scale and scope of this kind of enterprise data movement makes the risk too big to simply ignore,” said Derek Brink, vice president and research fellow, Aberdeen Strategy & Research. “Defining and extending the trusted network, while also providing visibility into potentially risky data movements to unmonitored devices and locations, are key capabilities going forward for managing Insider Risk to an acceptable level.”
Learn More About Code42 Incydr
The Code42 Incydr product allows security teams to effectively mitigate data exposure and exfiltration risks without disrupting legitimate collaboration. Incydr is purpose-built to help security teams effectively manage the dynamic nature of Insider Risk – that includes prioritizing and responding appropriately to the risks that matter the most. It surfaces the top indicators of Insider Risk and gathers detailed security intelligence about on- and off-network file movements.
Additional Resources
- Gather deeper background information on Code42’s Trust Model.
- Take a spin through an interactive demo of Incydr in our free sandbox environment.
- Join the conversation with Code42 on our blog, LinkedIn, Twitter and YouTube.
- Read our book, Inside Jobs: Why Insider Risk is the Biggest Cyber Threat you can’t Ignore.
About Code42
Code42 is the Insider Risk Management leader. Native to the cloud, the Code42® Incydr™ solution rapidly detects data loss, leak and theft as well as speeds incident response – all without lengthy deployments, complex policy management or blocking employee productivity. With Code42, security professionals can protect corporate data and reduce insider threats while fostering an open and collaborative culture for employees. Backed by security best practices and control requirements, the Code42 Incydr solution is FedRAMP authorized and can be configured for GDPR, HIPAA, PCI and other regulatory frameworks.
More than 50,000 organizations worldwide, including the most recognized brands in business and education, rely on Code42 to safeguard their ideas. Founded in 2001, the company is headquartered in Minneapolis, Minnesota, and is backed by Accel Partners, JMI Equity, NewView Capital and Split Rock Partners. Code42 was recognized by Inc. magazine as one of America’s best workplaces in 2020 and 2021. For more information, visit code42.com or join the conversation on our blog, LinkedIn, Twitter and YouTube.
© 2021 Code42 Software, Inc. All rights reserved. Code42, the Code42 logo and Incydr are registered trademarks or trademarks of Code42 Software, Inc. in the United States and/or other countries. All other marks are properties of their respective owners.
View source version on businesswire.com: https://www.businesswire.com/news/home/20210913005592/en/
Contacts
Press Contact:
Kristin McKenzie
Public Relations Principal, Code42
kristin.mckenzie@code42.com
844-333-4242













