The communication network is a complicated system comprising numerous software, hardware, and data systems. Their confidentiality, integrity, and availability provide the foundation for the network’s secure operation. However, there is an increasing trend of diverse network security threats. As a result, communication networks must be resilient and resistant to network security attacks and interference, which brings challenges to both equipment suppliers and operators. As a global telecom industry leader, ZTE prioritizes security and has established an effective security governance system, covering the entire product life cycle.
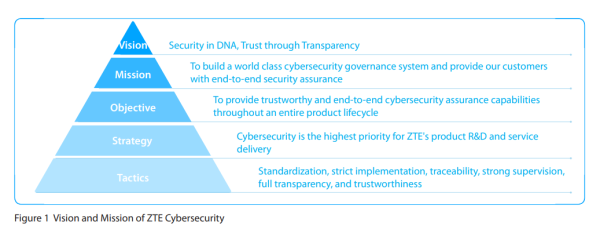
ZTE’s security mission is “security in DNA, trust through transparency.” ZTE is committed to offering customers safe and trustworthy products and services while adhering to laws and regulations, industry standards, and customer expectations, ultimately enabling connectivity and trust everywhere.
Businesses and organizations require extremely efficient risk management via mature governance architecture. The Institute of Internal Auditors (IIA) three lines model assists enterprises or organizations in identifying the most useful management structure and processes to achieve goals and clarifies all stakeholders’ respective roles and responsibilities in order to support governance and risk management more effectively.
To strengthen security governance, ZTE has established an organizational architecture based on the three lines model. It successfully ensures security from diverse views and levels through the first line’s self-inspection, the second line’s independent security evaluation, and the third line’s security audit.
Taking the second line as an example, the Product Security Department of ZTE is the company’s second line of defence regarding security governance. It is in charge of promoting the implementation of all management and technical practices related to security , coordinating the development of security policies and procedures, inspecting security implementation, and supervising and evaluating and the progress of the first line. The department provides security empowerment and professional support to business units, aids business units in risk management, and performs independent security assessments to analyze and monitor front-line security operations.

Process and product evaluation are part of the independent security assessment. The former is used to assess the compliance and effectiveness of business units’ security governance implementation processes, while the latter is used to analyze and assess the security of products and systems, including vulnerability scanning, code review, protocol robustness testing, and penetration testing.
The Product Security Department implements closed-loop monitoring and tracking of issues discovered during independent security audits. If any breach of product security red lines is discovered during the security assessment, the Product Security Department has the authority to immediately suspend the corresponding business activity until the product teams completely resolve the reported security issues.
In addition, ZTE actively collaborates with third-party organizations to assess the security of ZTE products, such as source code review, security design review, and penetration testing.
Besides, ZTE has developed strong security policies, standards, procedures, and guidelines. security policies define the fundamental needs for security governance. ZTE has also published a set of security management guidelines and specifications, which are reviewed regularly. Each business unit performs actual security actions in accordance with these security criteria. During the implementation phase, corresponding results and records are retained as proof for auditing by relevant parties.
ZTE places a high value on the development of security knowledge and skills. It has established a comprehensive talent development mechanism that combines career development and training for specialized security personnel in security standards, security planning, design, coding, security tools, penetration testing, security operation and maintenance (O&M), and so on. More than 170 staff held international security certificates by Q3 2021, including the CISSP, CISA, CISM, CSSLP, CEH, and OSCP, to mention a few. They help to increase the overall security governance level and security teams’ capacity.
Furthermore, ZTE has a custom of promoting various security-related information to all employees, such as security news, cutting-edge security technologies, best practices, and organizing security technology conferences, security open days, case study sharing, and other activities. Security awareness education permeates employees’ daily work through a variety of engaging activities.
The issue of network security is a tough task for the whole telecommunication industry. It requires more enterprises and operators to shoulder their responsibility, just as ZTE does, to develop effective mechanisms to ensure safe products and services.
Media Contact
Company Name: ZTE Corporation
Contact Person: Lunitta LU
Email: Send Email
Country: China
Website: https://www.zte.com.cn/global/














